Preparation
Create Cognito Identity Pool
- Open Amazon Cognito console, select Federated identities
- Click Create new identity pool
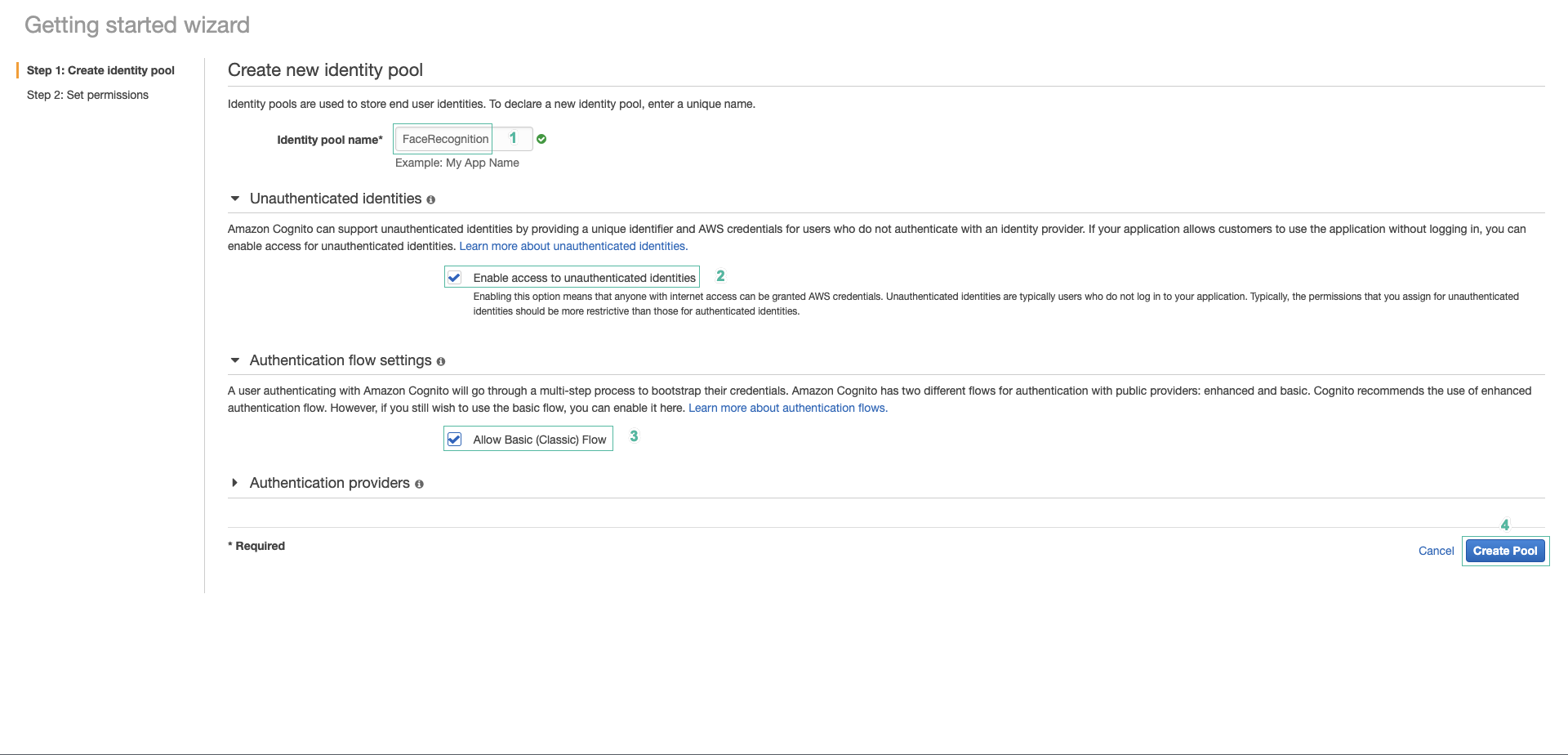
- In Identity pool name, select FaceRecognition. Check to 2 checkboxs Unauthenticated identities and Authentication flow setting.
- Click Create Pool
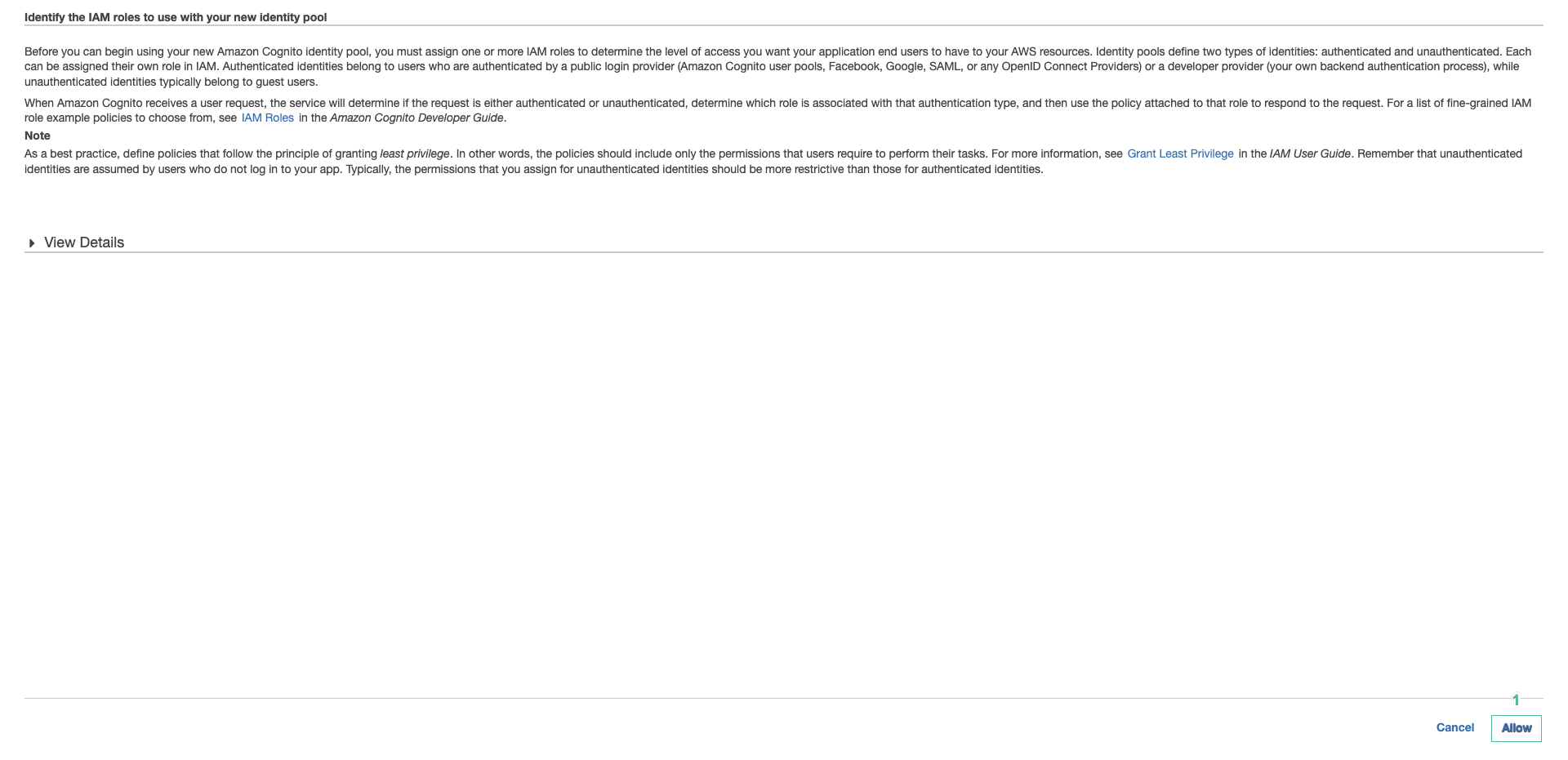
- In Identity the IAM roles to use with your new identity pool page, click Allow
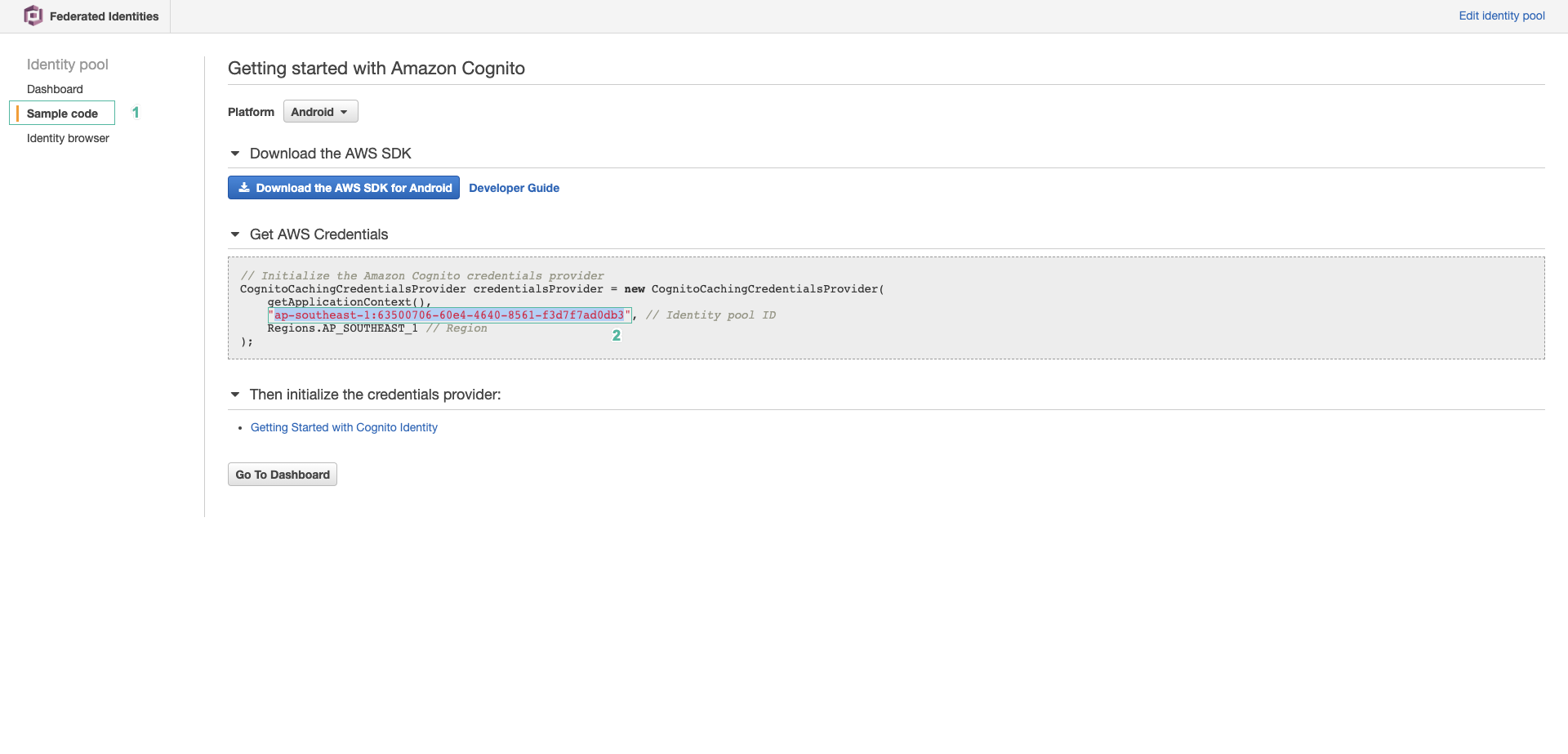
- Copy Identity pool ID, we will use it in the following steps
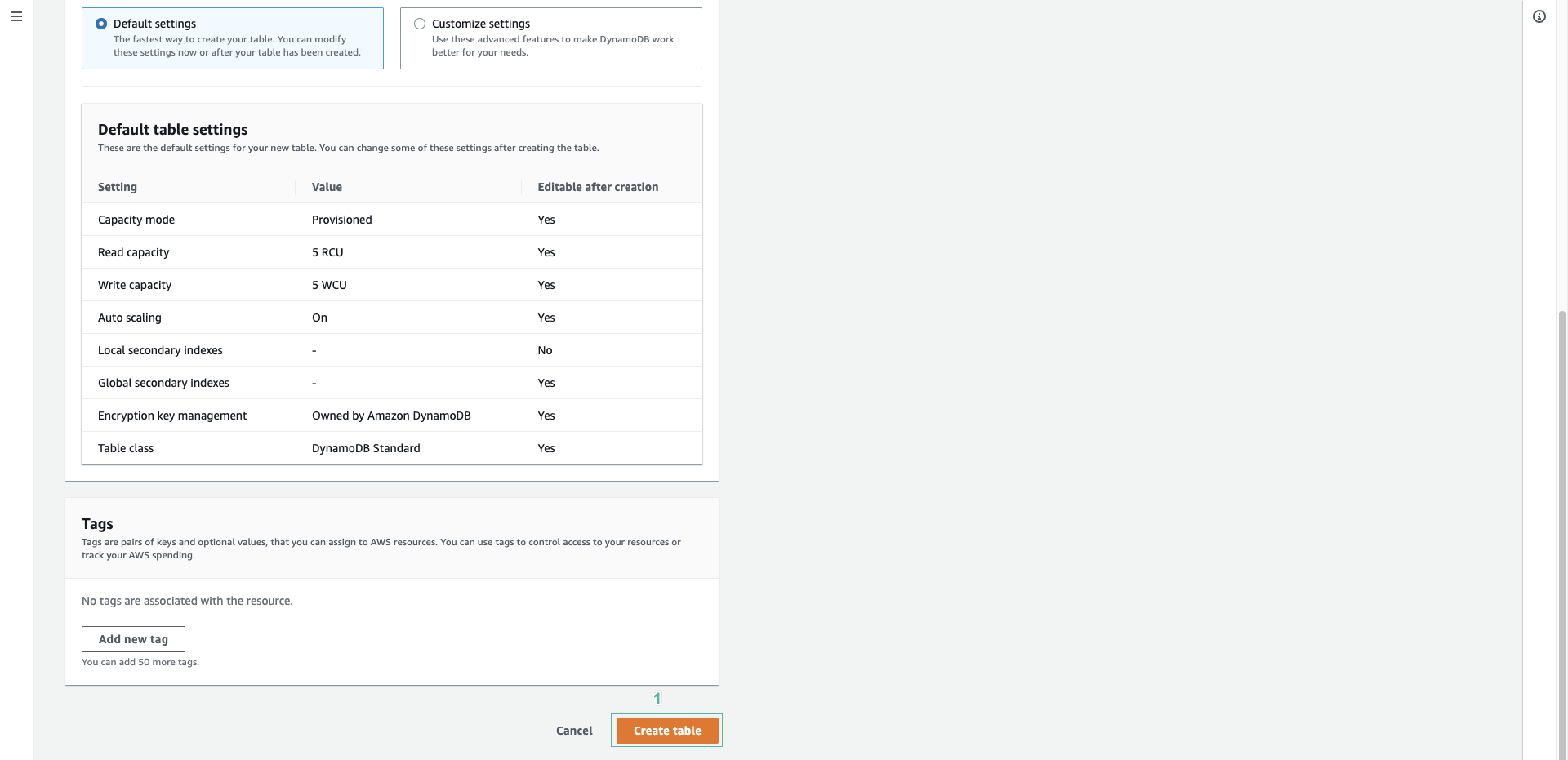
Create DynamoDB table
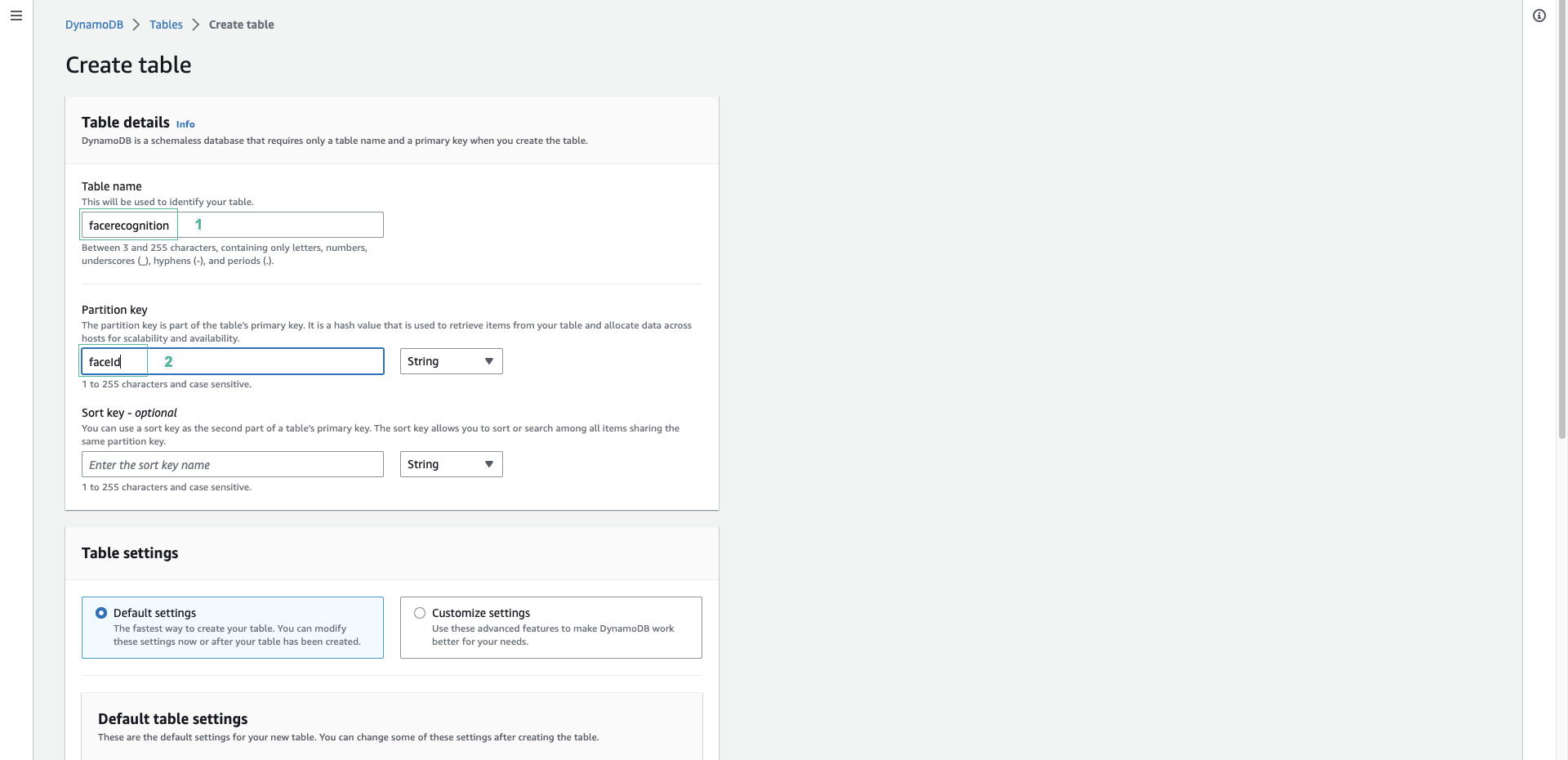
- Access AWS DynamoDB, click Create table.
- In Table name section, enter facerecognition
- In Primary key section, enter faceId.
- Then scroll to the bottom of the page and press Create table.
Create S3 bucket
- We will create 2 S3 buckets, a m7www bucket containing the website source code and a facerecognitions3bucket bucket containing image data for identification.
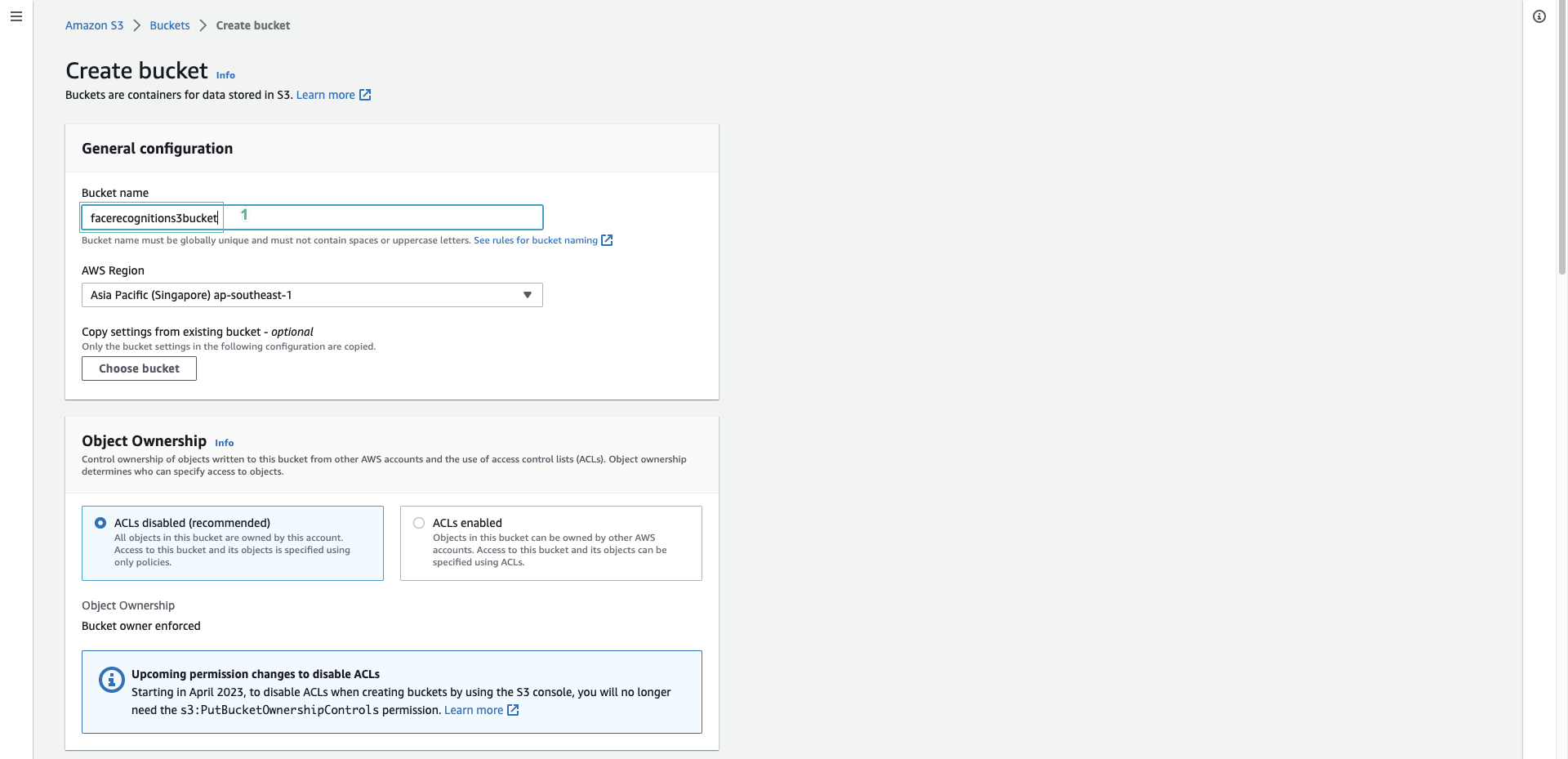
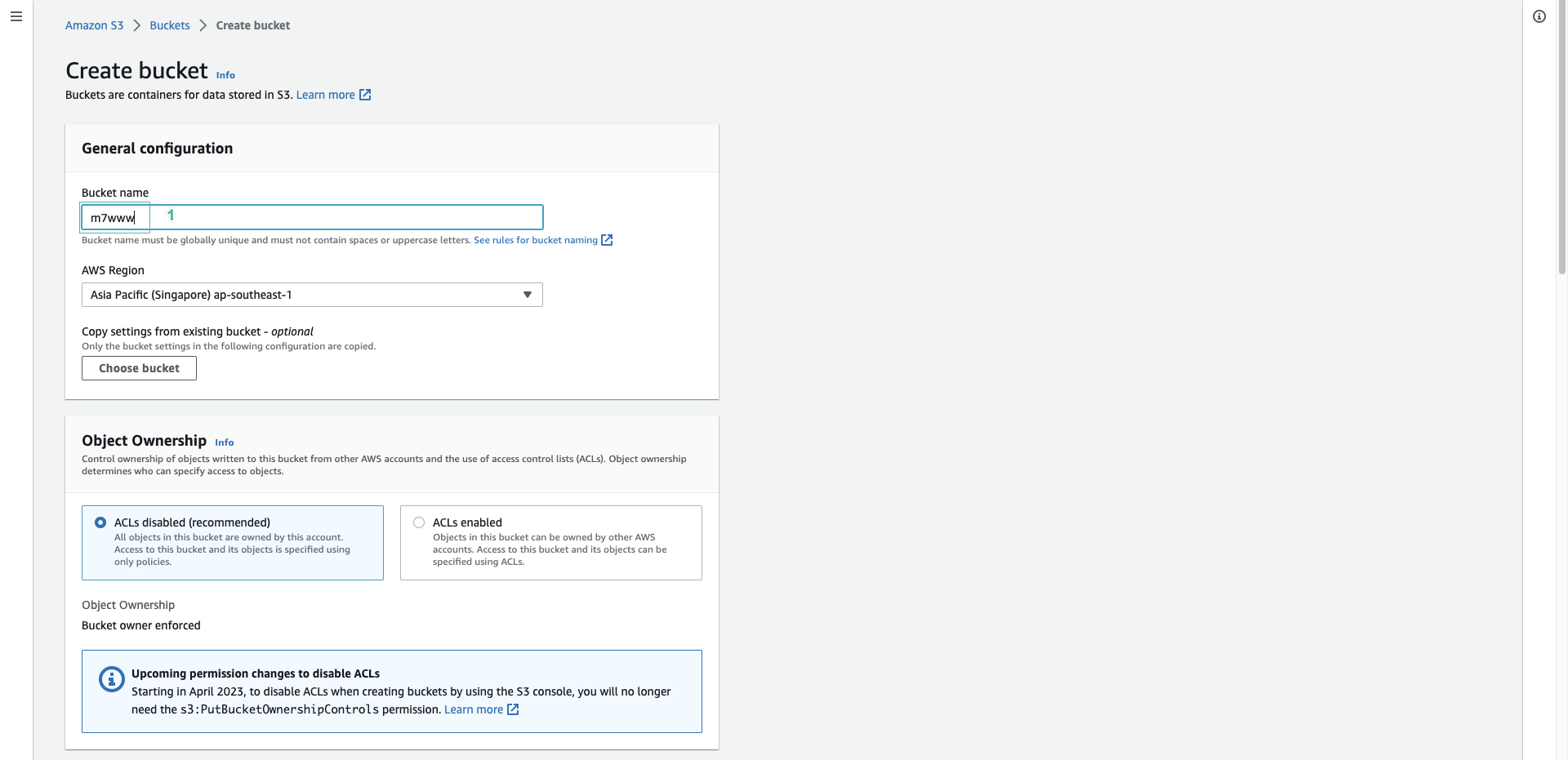
Uncheck Block Public Access settings for this bucket checkbox.
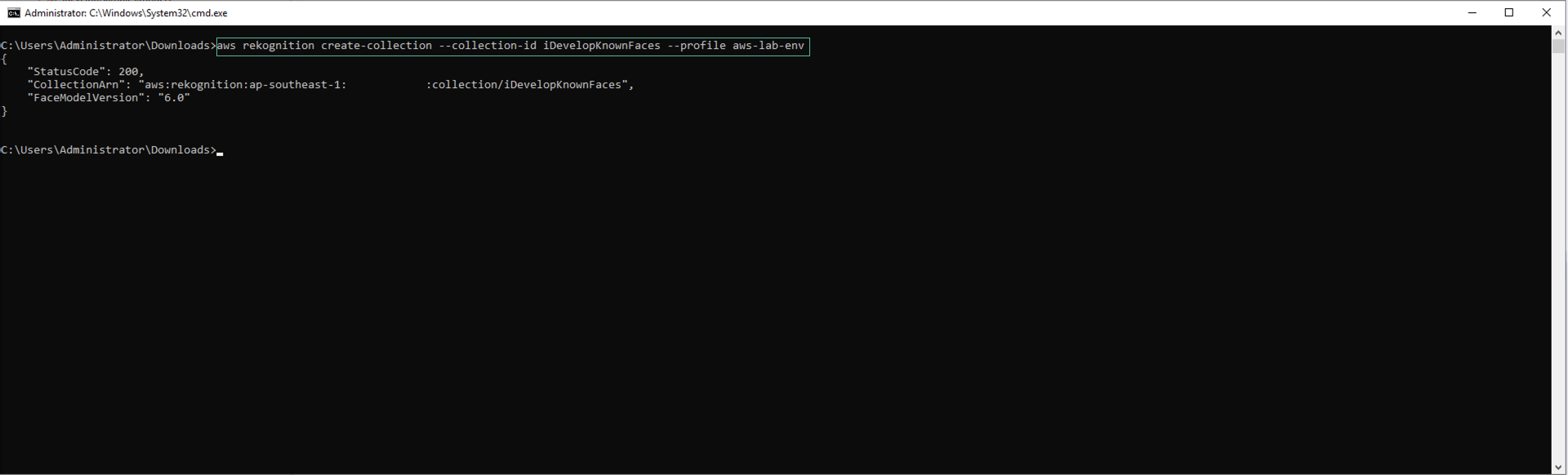
Create Rekognition Collection
- Use the following CLI command to create the iDevelopKnownFaces collection:
aws rekognition create-collection --collection-id iDevelopKnownFaces
Authorize Cognito
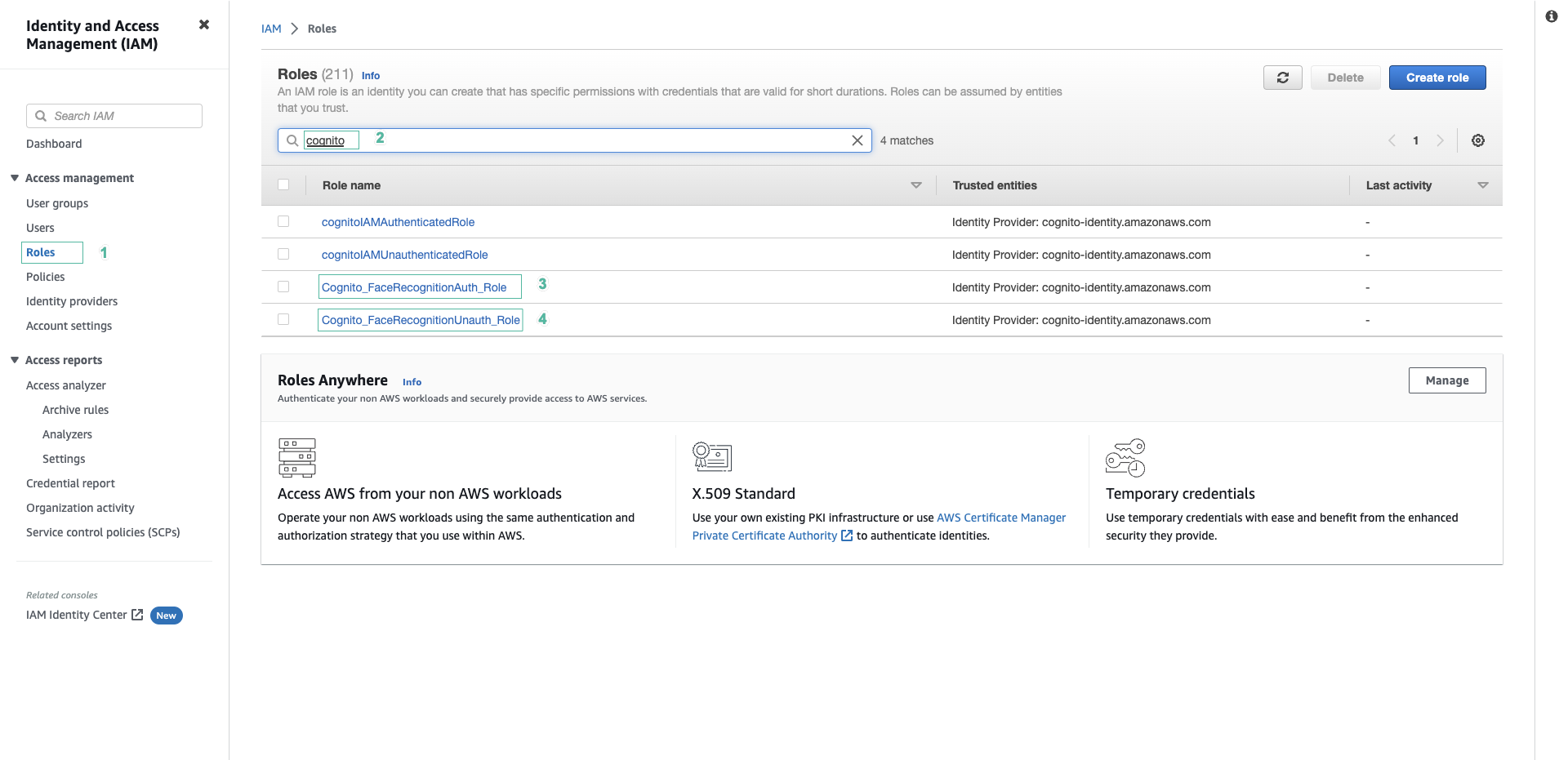
- Go to Amazon IAM console, select Role, search by keyword
Cognito. We will see 2 Roles Cognito_FaceRecognitionAuth_Role and Cognito_FaceRecognitionUnauth_Role of Cognito Identity Pool that we created in the previous step, we will edit the policy of these 2 Roles.
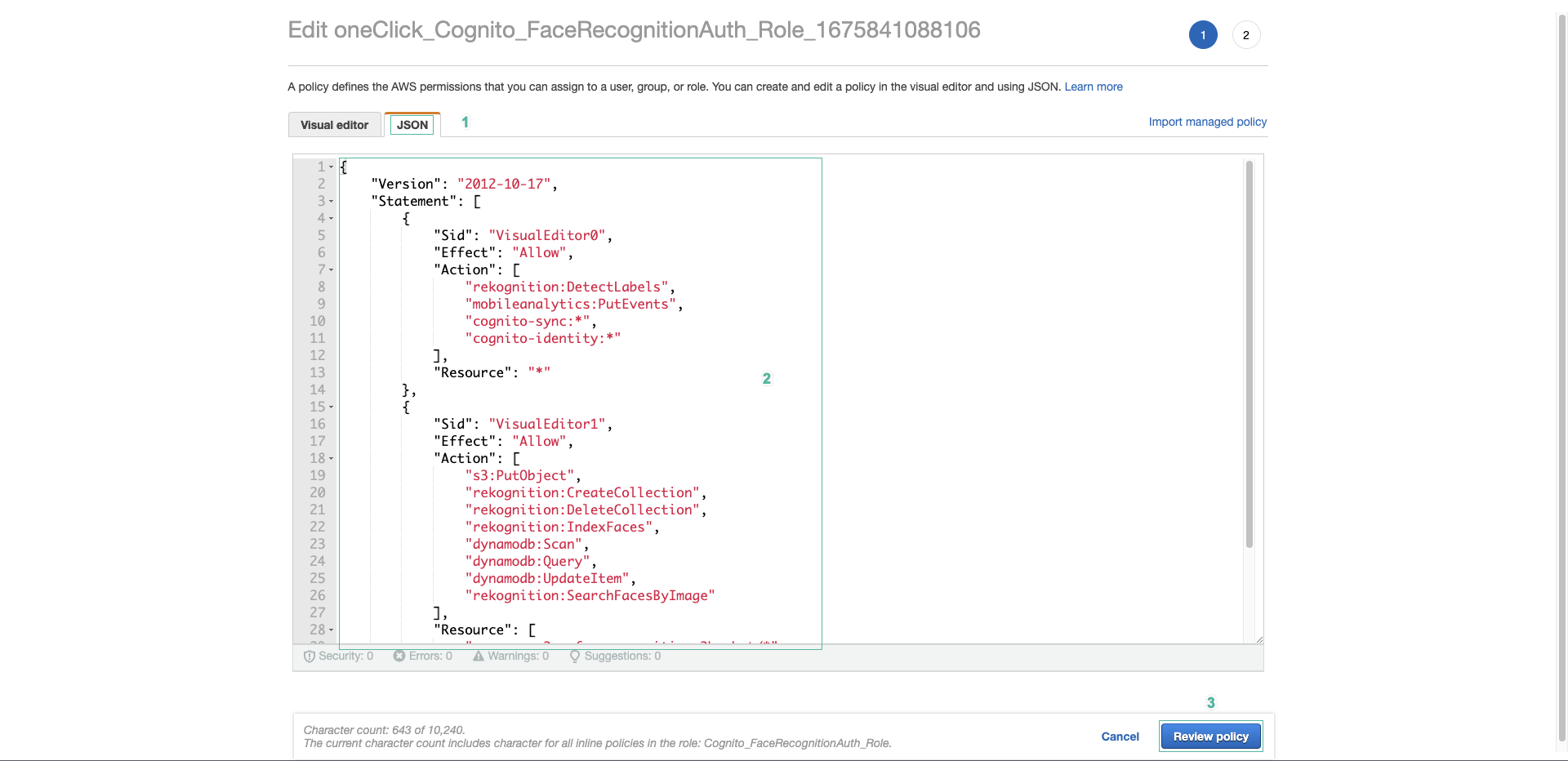
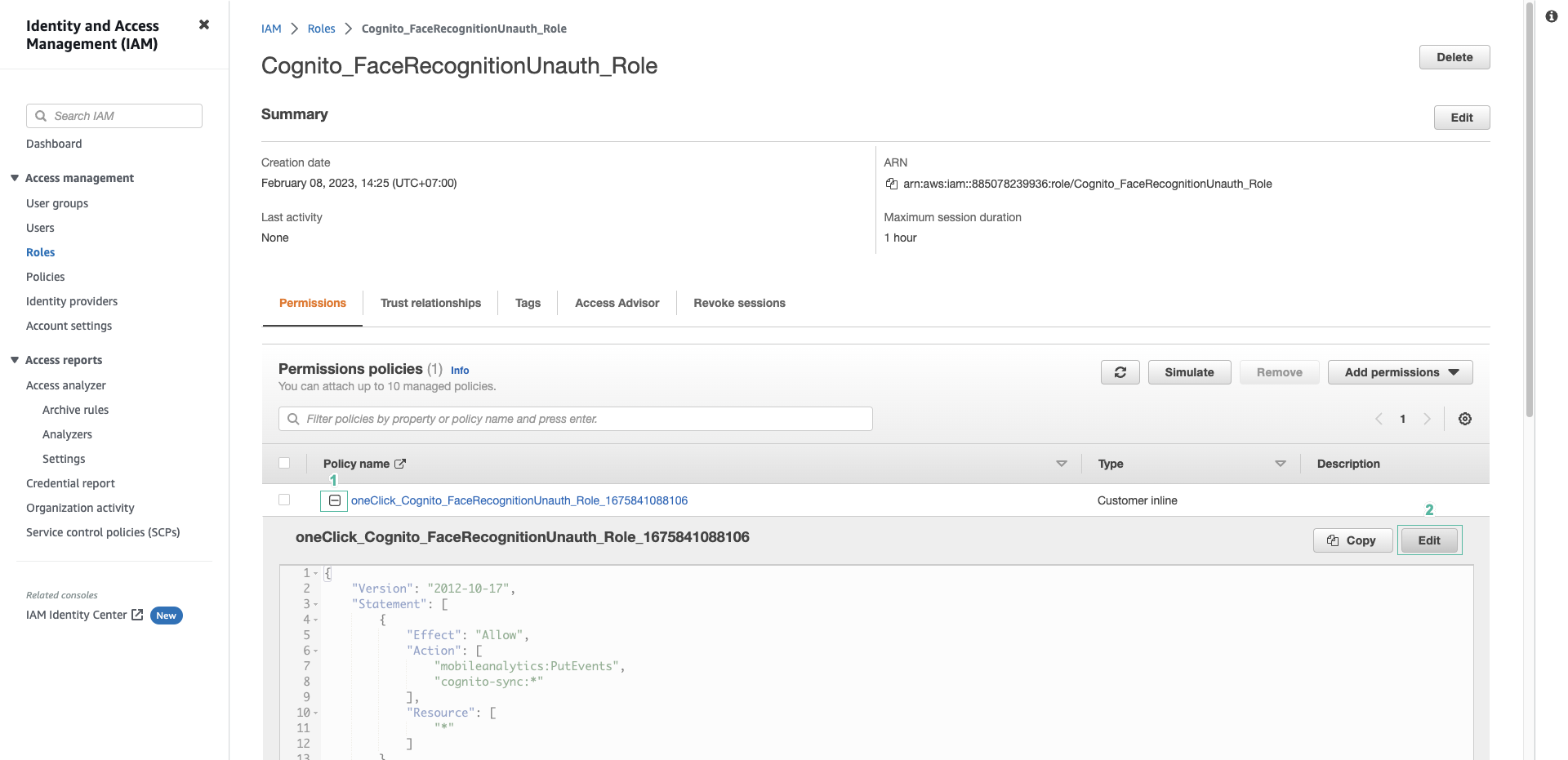
- Select Cognito_FaceRecognitionUnauth_Role, in Permision section, select oneClick_Cognito_Cognito_FaceRecognitionAuth_Role_xxxxxxxx, click Edit policy
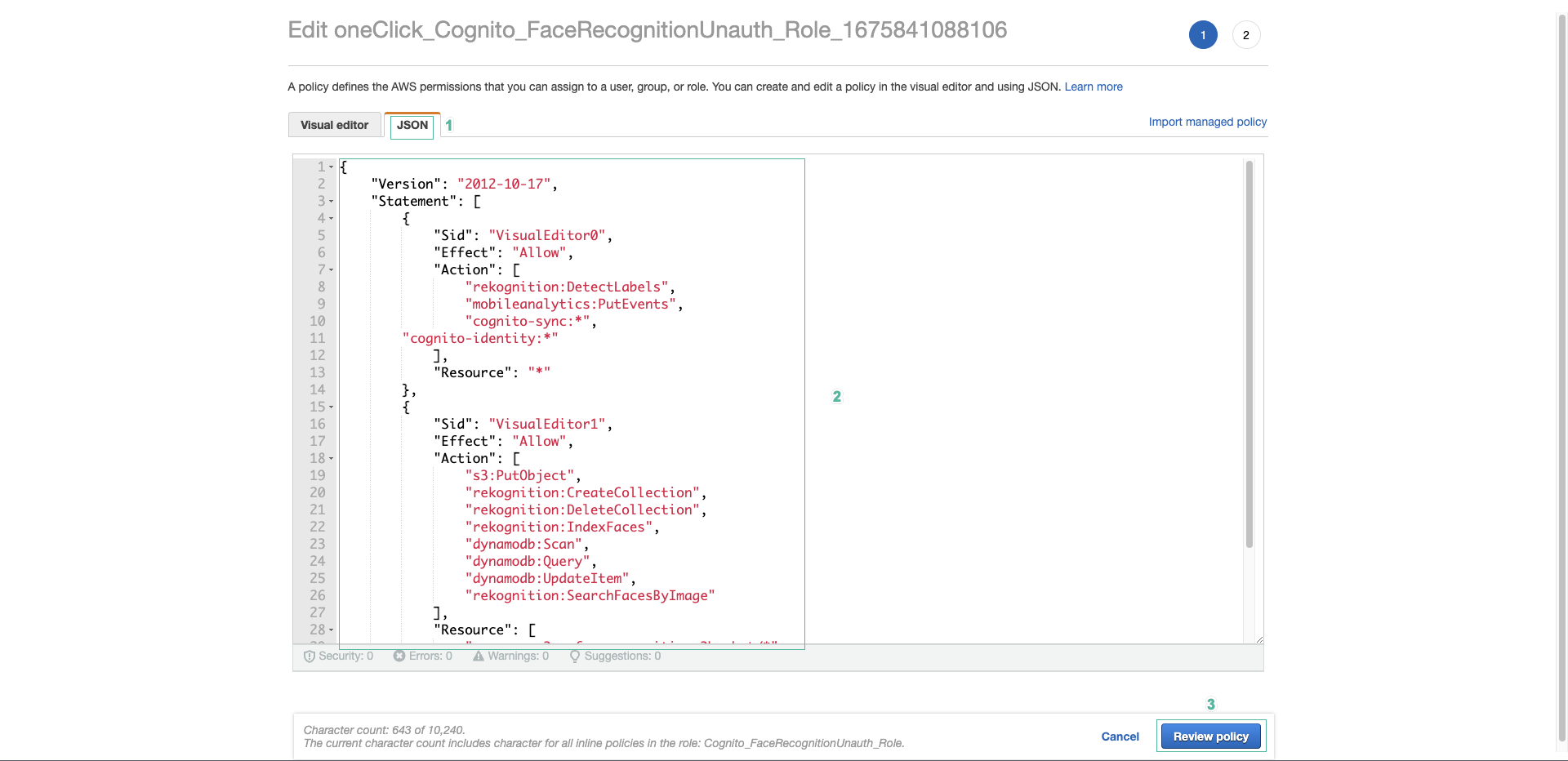
- Copy and paste the following into the JSON tab
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"rekognition:DetectLabels",
"mobileanalytics:PutEvents",
"cognito-sync:*",
"cognito-identity:*"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"rekognition:CreateCollection",
"rekognition:DeleteCollection",
"rekognition:IndexFaces",
"dynamodb:Scan",
"dynamodb:Query",
"dynamodb:UpdateItem",
"rekognition:SearchFacesByImage"
],
"Resource": [
"arn:aws:s3:::facerecognitions3bucket/*",
"arn:aws:dynamodb:<YOUR_REGION>:<ACCOUNT_ID>:table/facerecognition",
"arn:aws:rekognition:<YOUR_REGION>:<ACCOUNT_ID>:collection/iDevelopKnownFaces"
]
}
]
}
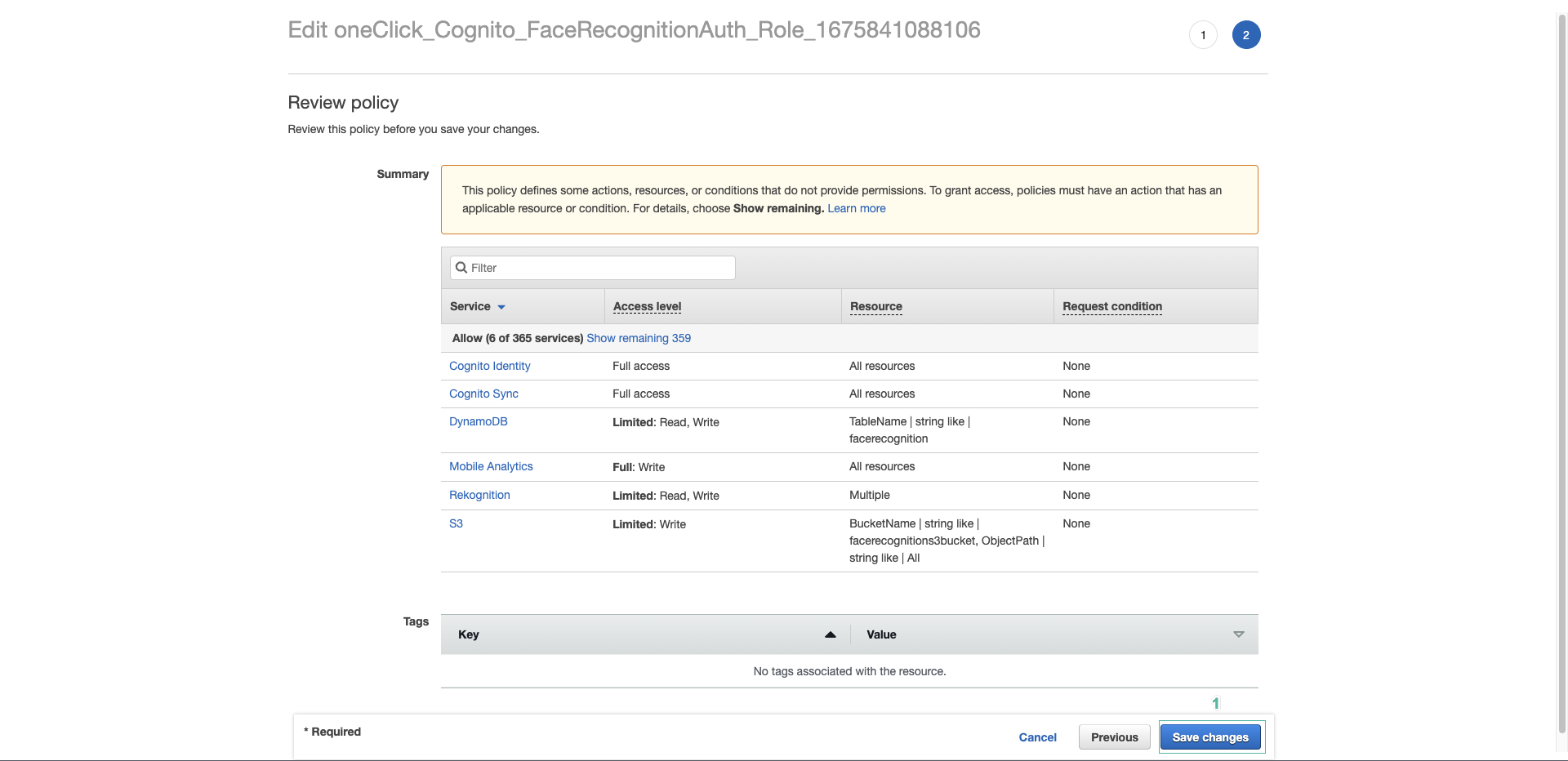
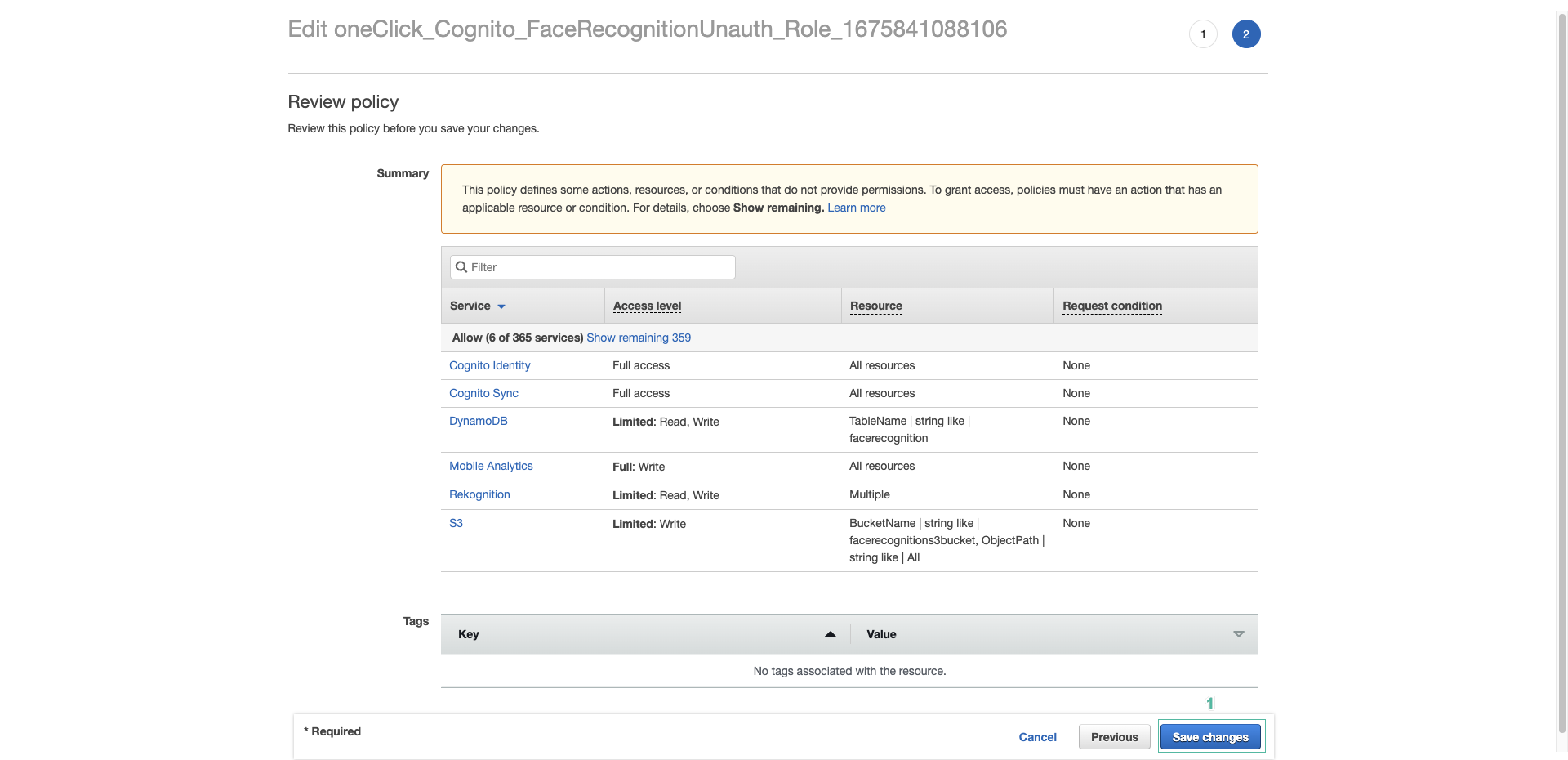
- Click Review Policy.
- Then click Save changes.
- Do the same with Cognito_FaceRecognitionAuth_Role
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"rekognition:DetectLabels",
"mobileanalytics:PutEvents",
"cognito-sync:*",
"cognito-identity:*"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"rekognition:CreateCollection",
"rekognition:DeleteCollection",
"rekognition:IndexFaces",
"dynamodb:Scan",
"dynamodb:Query",
"dynamodb:UpdateItem",
"rekognition:SearchFacesByImage"
],
"Resource": [
"arn:aws:s3:::facerecognitions3bucket/*",
"arn:aws:dynamodb:<YOUR_REGION>:<ACCOUNT_ID>:table/facerecognition",
"arn:aws:rekognition:<YOUR_REGION>:<ACCOUNT_ID>:collection/iDevelopKnownFaces"
]
}
]
}